Hackers and Hostilities: The Role of Cyber Espionage in Global Conflicts

March 12, 2024 Puloma Pal
What is Cyber espionage?
Cyber espionage refers to a kind of hack where the objective is to get or pilfer intellectual property (IP) or sensitive or classified material for purposes of competition, politics, or the economy. Cyber spies get into their targets' networks or devices using a variety of strategies, including proxy servers, cracking tools, and malicious malware. Cyber espionage may have an impact on people, businesses, governments, and other entities that hold important data. Cyber espionage victims may suffer from monetary loss, damage to their image, or even legal culpability.
Historical context of Cyber-attacks in Global conflicts
Spying over another is not new, but the method is. Since the ancient era, spies have been used to know the secrets of enemy states. During the contemporary period, spying methods were improvised. During this era, especially during World War 1 and 2, spying over another country was common. Hence, advanced technologies were used. For example, various devices like aerial cameras, observation planes, and CORONA (a 1st generation satellite). Today, this has changed, and technologies have made spying a lot easier. With the increase in smart phone users, hacking has become quite easier.
The origins of Cyberattack may be traced back to self-replicating programs in the 1970s and 1980s. In Pakistan, the Brain, the first PC virus, was developed in 1986. The first inkling of what was to come was offered by the Morris Worm in 1988. As computer got more networked, viruses could infect them more easily. The initial assaults disseminated harmful malware using popular Internet apps like email. As the Internet developed into a potent instrument for trade and dialogue, new kinds of attacks appeared. Attacks that are specifically aimed at have led to the theft of billions of dollars, hacked accounts, lost intelligence, power disruptions, and physical harm to equipment in safe places.
Cyber espionage attacks have the potential to interfere with vital services that impact homes, companies, and emergency services, such as communication networks and power grids. Financial institution assaults, intellectual property theft, and trade secret theft all have negative economic effects that lower investor confidence, raise cybersecurity expenses, and result in job losses. International collaboration, commercial ties, and diplomatic endeavours can all be hampered by a damaged national reputation. Cyber espionage frequently targets government activities with the goal of breaching communication and secret information systems. Theft of classified military information can give enemies a tactical edge and weaken a country's defence capacity. Both military and diplomatic communications can be jeopardised by compromised communication networks. Cyber espionage has the potential to directly affect military capabilities by breaching defence systems and breaking into military networks. Moreover, it has the power to subvert democratic processes, resulting in social dissatisfaction and political instability. Integrated cybersecurity policies that include technological advancements, international collaboration, governmental actions, and awareness initiatives are necessary to counter these threats.
For instance, Israeli and American intelligence collaborated to construct the powerful computer worm Stuxnet, which was intended to thwart the nuclear ambitions of Iran. It was accidentally distributed when it was first intended for an air-gapped facility, which begged the issue of its intent. Stuxnet, code-named "Operation Olympic Games," was designed to take down Iran's centrifuges that refine uranium. It caused significant harm and delayed the country's nuclear program by a minimum of two years. The virus showed a high degree of expertise by taking advantage of many zero-day vulnerabilities in Siemens PLCs and Windows. The identity of those who created Stuxnet is still unknown; however, it is thought to have been a team effort comprising highly qualified professionals. The unanticipated spread of Stuxnet beyond the intended location led to increased cybersecurity concerns and ultimately to its detection. Even though Stuxnet was a major advancement in cyberwarfare, it is no longer a serious danger. Notable for being the first instance of computer code being used in an international battle, it also served as an inspiration for other malware families. The event emphasizes how digital warfare is changing, impacting how the conflict between Russia and Ukraine unfolded later on and solidifying Cyberattack as a legitimate tactic in contemporary combat.
Cyber Espionage provides attackers access to diplomatic correspondence, military plans, and confidential government data, giving them the power to influence decisions, obtain an advantage over rivals, or even blackmail targets. Furthermore, trade secrets and intellectual property theft are forms of economic and industrial espionage that have a direct effect on a nation's innovation and economic competitiveness.
Another issue with critical infrastructure risk is that cyber criminals might attack banking, communication, and energy infrastructures, which could interrupt vital services and endanger public safety. Cyber espionage is a vital component of contemporary military and defence strategy, serving to collect intelligence, keep an eye on adversaries' movements, and disrupt hostile forces. Foreign relations are strained by discoveries of cyber espionage, which can lead to political unrest, sanctions, or retribution. The consequences go beyond national security strategy and diplomacy. Countries that rely heavily on internet infrastructure for technology are more vulnerable because attackers can take advantage of new vulnerabilities that arise from the ongoing demand for innovation.
Moreover, non-state entities add to the intricacy of cyber espionage, such as hacktivist groups and cybercriminal enterprises. They muddy the distinctions between activities supported by the state and those that are not, making attribution difficult and complicating the implementation of efficient national solutions. In order to protect national interests, it is imperative that digital domains be addressed and secured, since the panorama of cyber threats continues to evolve.
Types of Cyber Espionage
A. State-sponsored cyber espionage occurs when an unauthorized user tries to get confidential or classified information or intellectual property (IP) for financial benefit, a competitive edge, or political purposes. Organizations that utilize obsolete software with recognized weaknesses are frequently the focus of state-sponsored threat actors. State-sponsored cyber espionage is carried out with the intention of outwitting rival nations or organizations strategically or economically. Aside from stealing sensitive data and communication systems, state-sponsored cyber espionage may also jeopardize military operations.
B. Corporate cyber espionage occurs when an unauthorized user tries to get access to private or sensitive information or intellectual property (IP) that belongs to a business or organization. Corporate cyber espionage may have major economic repercussions. It may lead to the compromise of business secrets, proprietary information, and other private data, which might be detrimental to the standing and financial success of an organization. ECIPE estimates for 2018 indicate that trade secret cyber theft might cost Europe alone roughly 289,000 jobs and €60 billion in lost economic growth. Digitalization increases the risk, and losses are predicted to equal one million employment by 2025.
Global Conflicts and Cyber Espionage
Global wars shape the geopolitical landscape, and cyber capabilities are a major factor in determining how states are positioned on the international scene. In light of developing cyber capabilities, nations may re-evaluate their geopolitical positions. As cyber capabilities are viewed as crucial elements of military and intelligence plans, alliances are becoming more dynamic and priorities are changing. Cyber espionage, which may gather private data and interfere with vital infrastructure, is one national security threat. To stay ahead of technology, nations spend a lot of money building offensive and defensive cyber capabilities. Severe economic repercussions, such as trade interruptions and the theft of trade secrets and intellectual property, are among the economic ramifications. Cyber capabilities are invested in by nations for both innovation and defence. Establishing repercussions, defining rules of engagement, and creating laws specifically for the internet are among the difficulties that international law and norms must overcome. Response diplomacy and difficulties with attribution also strain diplomatic relations. Preventing miscommunications and promoting collaboration require the establishment of global standards for appropriate online conduct.
How Ukraine is facing Cyber Espionage
Russian digital operations have an extensive past and are mostly focused on espionage and political warfare. Prior to 2014, the main targets of Russia's efforts were Estonia and Georgia. Information operations against Georgia were made possible in 2007 and 2008 by denial-of-service attacks. Global logistics were impacted by the NotPetya campaign, which was started in 2017 by parties with ties to Russia. Additionally, Russia has employed propaganda to polarize society and sway elections through cyberwarfare. Campaigns of simultaneous disruption were employed to vandalize websites and depict pro-Ukrainian activists as Nazis. In an effort to erode trust in American democracy, actions aimed at the presidential election were started in 2016. The U.S. Cyber Command justified a pre-emptive operation against the Internet Research Agency in 2018 by citing Russia's prior actions and concerns. In recent years, complex espionage and illicit malware operations have been merged into Russian operations. The year 2020, saw the Russian hacker organization APT29 steal data and digital tools from many targets by taking advantage of a supply chain vulnerability in the Solar Winds Orion software. The infrastructure that transports petroleum throughout the East Coast of the United States was effectively targeted by ransomware in 2021, thanks to the actions of criminal actors going by the name of DarkSides. Around 30 dyadic cyber events between Russia and Ukraine were started by Russia between 2000 and 2020, according to the most recent edition of the Dyadic Cyber Incident and Campaign Data (DCID 2.0). Of these, 93% were started by Russia, while 57% of the victims were non-state, private entities. Phishing efforts, denial-of-service tactics, propaganda, and single network breaches were the most common characteristics of these attacks. None of these occurrences led to bodily harm that persisted or to concessions in Ukraine's actions.

(Figure 1: Russian Cyber objectives targeting Ukraine 2022, from CSIS)
How Israel is dealing with Cyber Espionage
Ever since the internet and information were first digitalized, Israel has struggled with cybersecurity challenges. Cyber threats increased throughout the 1990s, mostly in the form of hacking and the defacement of websites. Attacks against Israeli networks increased in the early 2000s, and these attacks were frequently attributed to state-sponsored actors and hacktivist organizations. The 2010 Stuxnet revelation increased public awareness of the possibility of real-world repercussions from Cyberattack. Israel is always under attack from a range of state-sponsored entities, and the Middle East's geopolitical context makes for a dangerous cyber environment. Advanced persistent threats, or APTs, aim to compromise security measures, research and development initiatives, and confidential government data. There is a greater emphasis on protecting crucial infrastructure from cyber-attacks, such as electricity amenities, water systems, and other essential utilities, because of Israel's geopolitical position and continuing conflict.
In the wake of recent lethal strikes, hacker groups—possibly connected to Russia—have started Cyberattack against media and government websites in Israel, identifying themselves with the Palestinian militant group Hamas. Killnet announced its plan to launch distributed denial-of-service (DDoS) assaults on Israeli government networks. The group claimed to be patriotic Russian hackers and blamed Israel for the war, accusing it of aiding NATO and Ukraine. Suspected to be a front group for Russia, Anonymous Sudan declared sympathy for the "Palestinian resistance" and took credit for momentarily knocking down the Jerusalem Post website. Other hacker organizations focused on Israeli infrastructure, such as missile warning systems and power plants.
According to cybersecurity experts, Russian hacktivist are taking advantage of the situation to back Hamas in the fight by launching DDoS assaults in order to make headlines. Many of the assaults against Israeli infrastructure claimed by various self-described hacktivist gangs could not be independently confirmed. A hacking collective known as AnonGhost gained access to an Israeli missile alert app and replaced its phony notifications with swastikas and anti-Israel language. In response, pro-Israel organizations launched Cyberattack on Palestinian institutions. One such group, the Indian Cyber Force, claimed to have taken down the websites of Hamas and the Palestinian National Bank.
Hacking troops from Iran may or may not be involved in the ongoing battle, but suspicions of Iranian involvement have been levelled at Israel, a country that is frequently the subject of Cyberattack. Although the impact of the hacks has been minimal thus far, experts warn that things might change. Rob Joyce, the head of cybersecurity for the National Security Agency, observed brief denial-of-service assaults and minor online defacements but said that there was no significant cyber component to the fight. He does, however, note that more hacktivist efforts in favour of different causes can be possible, and that effect might not always depend on skill.
India and Cyber Espionage
The NDA government, under the leadership of PM Modi, focuses on the digitalization of the country. Though these initiatives have been praised and criticized by people in and around the country, but as per the data and reports, 1) many Indians lack knowledge of computers; 2) the literacy level is still not well; and 3) the statistics of cyber theft or stealing personal data in India are quite alarming. Hence, the question here arises: how well is India prepared for cyber espionage in its own home?
According to cyber security company Check Point, India saw a rise of 15% in every week cyber assault instances in 2023, second only to Taiwan in the Asia Pacific area. There were 1,158 weekly average Cyberattack worldwide, up 1% from 2022. In 2023, 2,138 attacks per organization were made against India, making it the second most targeted country in Asia after Taiwan. With a 15% increase, the nation saw the second-highest spike in attacks since 2022, after Korea with a 21% increase. With an average of 1,930 attacks per organization, APAC had the highest average weekly attack count. Attacks against the retail and wholesale sectors increased by 22%, while attacks against the education and research sectors decreased by 12%. The critical nature of the healthcare sector makes the 3% increase in attacks particularly concerning .
As India’s digital foot print expands, danger of cyber theft increases too. As per various reports and News articles, around 83% of Indian companies face cyber related incidents previous year. For example, a Power Grid in Ladakh was a state sponsored cyber-attack. As per the reports published by Recorded Future, an American cybersecurity firm, wrote that there were several campaign’s launched or conducted which are likely done by the Chinese’s state – sponsored attack groups. These groups have attacked Indian Power grid multiple time. There are reports published by another security firm, based in Massachusetts, which has described multiple cyber - attack by SHADOWPAD, a malware on STATE LOAD DESPATCH CENTRE (SLDC’s). Further the report claimed that these hackers are supported by China. It also wrote in the report that these group of hackers often use Trojan ShadowPad which has further linked with People’s liberation army and the Ministry of State security of China. The report believed that these hacker groups – Threat activity group 38(or TAG) have also targeted the CERT –In and Multinational Logistics Company. In a meeting held in New Delhi, the Power Minister – RK Singh acknowledge the cyber-attack and assured that preventive measures to counter the cyber – attack were very strong. In short, due to India’s strong defense against the hackers, it prevented the attack to get worse and stopped the hackers to steal sensitive data.
It is quite obvious that the Chinese government denied all such claims and any reports that threatened the image of China and its government. A statement released by the embassy of the People’s Republic of China in Gambia describes how the Chinese’s spokesperson, Zhao Lijian, answered a question asked by a representative from Macau Monthly. In this media briefing, which was held in Beijing, Zhao Lijian (the Spokesperson of China’s Foreign Ministry) said, “As I have repeated many times, we firmly oppose and crack down on all forms of hacking activities. We will never encourage, support, or condone such activities." - Zhao Lijian has denied all such reports that have claimed that the Chinese government is involved in hacking. He further said the US government has repeatedly been involved in Cyberattack on various countries. These countries, those who are allies with the US or those who cooperate on cyber security, have also been victims of US Cyberattack. Lijian also added that China is also a victim of US Cyberattack. The US government has, as per China, been pursuing “FORWARD DEVELOPMENT” around China (i.e., China’s neighbors). It has also been looking for military collaborations with neighbors of China in the cyberspace area. In short, the Chinese spokesperson has denied all the reports that claim the Chinese government.
Indian Government in Action
Various platforms and agencies have either been created or have been assigned tasks to be watchdogs and constantly keep a check on Indian cyberspace. The government’s initiatives, like spreading awareness regarding cyber, malware, etc. With 13 banks and internet service providers using the facility, India is expected to see a surge in cyber-security start-ups by the end of the year. The initiative, a Botnet Cleaning and Malware Analysis Center, was created through a collaboration between Cyber Swachhta Kendra and Quick Heal, who introduced a bot removal tool to help users remove botnet infections from their digital devices.
To combat cyber espionage and cybercrime, the government of India has come up with a comprehensive strategy. These strategies included wide-ranging initiatives, advisories, and training initiatives aimed at prosecutors, judges, and law enforcement officers. A digital platform was established which enabled victims to report their complaint. For example, the National Cyber Crime Reporting Portal, which was established in year 2019, aims to resolve victim’s complaint digitally. The National Critical Information Infrastructure Protection Centre (NCIIPC) guard’s information facilities and businesses providing digital services have an obligation to notify the Computer Emergency Response Team of India (CERT-In) of any incidents. Tools for removing malware are freely available from the Cyber Swachhta Kendra. A crisis management technique was established created to counteract cyber terrorism and Cyberattack. India also participates in Memoranda of Understanding (MoUs) and the Global Ransomware Initiative with other countries. The government uses a variety of communication platforms to educate the public and put an end to online financial scams.
Apart from the government, many institution-level initiatives have been made. For example, a collaboration between Kaspersky and IIT Bombay has been launched in order to advance cybersecurity training and study in India. The collaboration intends to improve the cybersecurity workforce through information exchange, the creation of instructional materials, and event planning. In addition, Kaspersky will fund medals and book rewards for students considering careers in cybersecurity. The MoU with IIT Bombay shows Kaspersky's dedication to bolstering cybersecurity internationally and utilizing the strengths of academics and industry.
Bottom Line
Today topics related to Cyber are quite trending. Technologies these days are becoming advanced. Cyberattack have an interesting history that closely tracks the development of digital technologies. During the 1940s, the first digital computer in history, was developed. During this period, Cyberattack were difficult to execute. This is because of the restricted access to these devices. Today, computers are readily available in the market. The computers we have today are cheaper and more advanced, and internet availability is around the globe. Hence, Cyberattack have become easy.
The idea of programs that may replicate or spread themselves was first introduced during the 1970s, marking the birth of computer security. The Brain, the original PC virus, was developed in Pakistan in 1986. During 1980, ARPANET to Internet Transition was the first commercial malware-examining antivirus software released in 1987. The Internet took off during the 1990s, and cases related to cybercrime rose as the internet became more widely available. In 2010, people saw the introduction of cyberwarfare with the launch of Stuxnet, the first computer virus designed to inflict physical harm.
The Cyber Espionage is the theft of personal information or confidential data. The hackers target individuals, companies or Critical infrastructure of countries to collect data which can be useful. The concept of stealing data from enemy has changed over time. During the ancient era, humans were trained to become spies. During the contemporary period, advance technologies were used. Today, spying over other nation or other business is one click away.
With advancement in technologies, cases of cyber espionage has increased. Countries like South Korea often faces Cyber-attacks from North Korea. As per the intelligence agency of South Korea, there was 36% of increase observed in cyber-attacks from its neighbour – North Korea. From previous year, Cyber-attack has been on rise. The cyber-attack in South Korea comprises of attacks from North Korea 80% and China around 5%. Cyber Espionage, as per Security magazine, has increased during the Covid 19 pandemic.
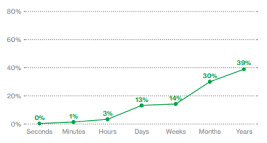
(Figure 2: Time to discovery within cyber espionage breaches from 2014 to 2020, Security Magazine)
In short we can say that, the Cyber advancements are like sharp weapons, the more we sharp them the more pointed they become and the more accurate aim it targets. India, who also faces cyber espionage, has been dealing with situations very well. To reduce cyber-attacks on critical infrastructure, India has come up with strategies. These strategies include establishing various taskforce like The National Counter Ransomware Taskforce (NCRT) and Defence Cyber Agency (DCA). The government is working hard to introduce new and strict laws. As per Lt. General Rajesh Pant (National Security Coordinator) (Telecom, 2024) pointed out the need to maintain “Cyber Hygiene”.
Though there is a lot of work for India to do. Also, it is important to note that no matter how well the government is, if the citizens themselves are not aware with cyber security or what measure need to be taken when their devices are been hacked, the rate of Cyberattack may increase.
Sources and References
Hewlett Packard Enterprise. (2020). what is Zero-Day Vulnerability? | Glossary. Hpe.com. https://www.hpe.com/in/en/what-is/zero-dayvulnerability.html#:~:text=A zero-day vulnerability is
Arin, K. (2024, January 25). Seoul’s spy agency accuses China of major cyber-attacks. Asia News Network; ANN Asia News Network. https://asianews.network/seouls-spy-agency-accuses-china-of-major-cyber-attacks/
Arkansas Democrat Gazette. (2023, October 10). Musk recommends questionable users | Arkansas Democrat Gazette. Https://Www.arkansasonline.com/News/2023/Oct/10/Musk-Recommends-Questionable-Users/; Arkansas Democrat Gazette. https://www.arkansasonline.com/news/2023/oct/10/musk-recommends-questionable-users/
BENE, N. (2011, November 2). The Man Who Found Stuxnet – Sergey Ulasen in the Spotlight. Eugene.kaspersky.com. https://eugene.kaspersky.com/2011/11/02/the-man-who-found-stuxnet-sergey-ulasen-in-the-spotlight/
Check Point. (2021). DarkSide Ransomware Group Explained. Check Point Software. https://www.checkpoint.com/cyber-hub/threat-prevention/ransomware/darkside-ransomware-group-explained/
CrowdStrike. (2021, April 1). What is Cyber Espionage? Targets, Tactics & More Explained | CrowdStrike. Crowdstrike.com. https://www.crowdstrike.com/cybersecurity-101/cyberattacks/cyber-espionage/
Fruhlinger, J. (2022, August 31). Stuxnet explained: The first known cyber weapon. CSO Online. https://www.csoonline.com/article/562691/stuxnet-explained-the-first-known-cyberweapon.html
GALLAGHER, R., & ROBERTSON, J. (2023, October 10). Cyberattack Targeting Israel Are Rising After Hamas Assault. TIME. https://time.com/6322175/israel-hamas-cyberattacks-hackers/
Goud, N. (2023, October 9). Israel Govt websites hit by DDoS Cyber Attack. Cybersecurity Insiders. https://www.cybersecurity-insiders.com/israel-govt-websites-hit-by-ddos-cyber-attack/
Griffiths, C. (2023). The Latest Cyber Crime Statistics (updated December 2023) | AAG IT Support. Aag-It.com. https://aag-it.com/the-latest-cyber-crime-statistics/#:~:text=The pandemic affected cyber security
Gülen, K. (2022, November 4). What Is Cyber Espionage: Examples, Types, Tactics, And More, Data Economy. https://dataconomy.com/2022/11/04/cyber-espionage-examples-types-tactics/
Krasznay, C. (2020). Case Study: the NotPetya Campaign. Research Gate. https://www.researchgate.net/publication/353072644_Case_Study_The_NotPetya_Campaign
Mueller, G. B., Jensen, B., Valeriano, B., Maness, R. C., & Macias, J. M. (2023). Cyber Operations during the Russo-Ukrainian War. Www.csis.org. https://www.csis.org/analysis/cyber-operations-during-russo-ukrainian-war
NotPetya (2017). (2019, May 17). International Cyber Law: Interactive Toolkit. https://cyberlaw.ccdcoe.org/wiki/NotPetya_(2017)
Dark, E. W. (2022, 04 08). China hackers targeted power grids near Ladakh, says report. China hackers targeted power grids near Ladakh. New Delhi, Delhi, India: The Indian Express. Retrieved 02 08, 2024, from https://indianexpress.com/article/india/chinese-hackers-electricity-distribution-centres-ladakh-minister-rk-singh-7858001/
Dark, E. W. (2022, 04 08). Indian Express. Retrieved from China hackers targeted power grids near Ladakh, says report: https://indianexpress.com/article/india/chinese-hackers-electricity-distribution-centres-ladakh-minister-rk-singh-7858001/
Express, T. N. (2024, 01 22). The New Indian Express. Retrieved 02 08, 2024, from The New Indian Express: https://www.newindianexpress.com/nation/2024/Jan/22/cyber-attack-cases-on-indian-entities-rise-15-pc-in-2023-check-point
Lijian, Z. (2022, 04 08). Embassy of People’s Republic of China in Gambia. Retrieved 02 07, 2024, from Embassy of People’s Republic of China in Gambia: http://gm.china-embassy.gov.cn/eng/wjbfyrth/202204/t20220408_10665857.htm
Yadav, V. (2023, 11 4). Zee News. Retrieved from The Big Challenge of Cybersecurity: How Indian Companies Are Facing Rising Threat Amid Relentless Attacks: https://zeenews.india.com/companies/the-big-challenge-of-cybersecurity-how-indian-companies-are-facing-rising-threat-amid-relentless-attacks-2684210.html
ET Telecom, (2023, 02, 21). Retrieved on Feb 16, 2023, from ET government: https://government.economictimes.indiatimes.com/news/governance/national-cybersecurity-strategy-2023-to-be-introduced-soon-rajesh-pant/98116674
About the Author:
Puloma Pal is working as a Research Intern at Indic Researchers Forum. She is currently pursuing her Master's in International Relations from Amity University, Noida.
Note:
This Article reflects the opinion of the author and not necessarily the views of the organisation.
Share this article:
© Copyright 2025 Indic Researchers Forum | Designed & Developed By Bigpage.in